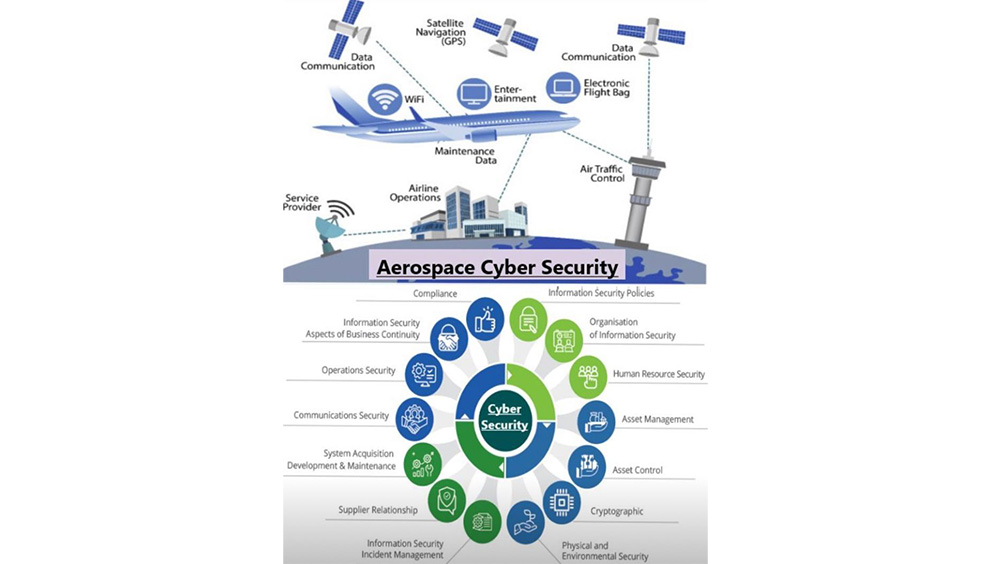
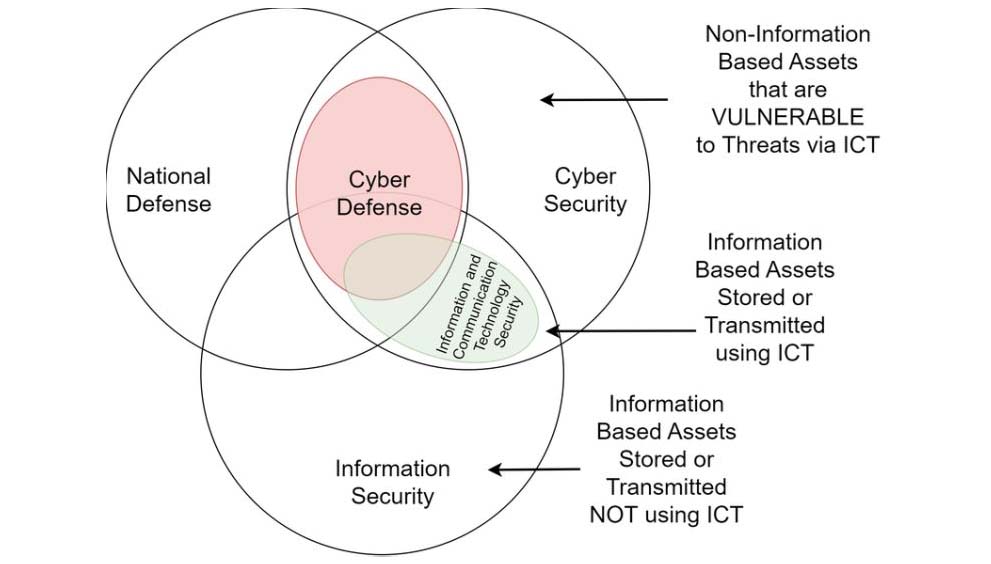
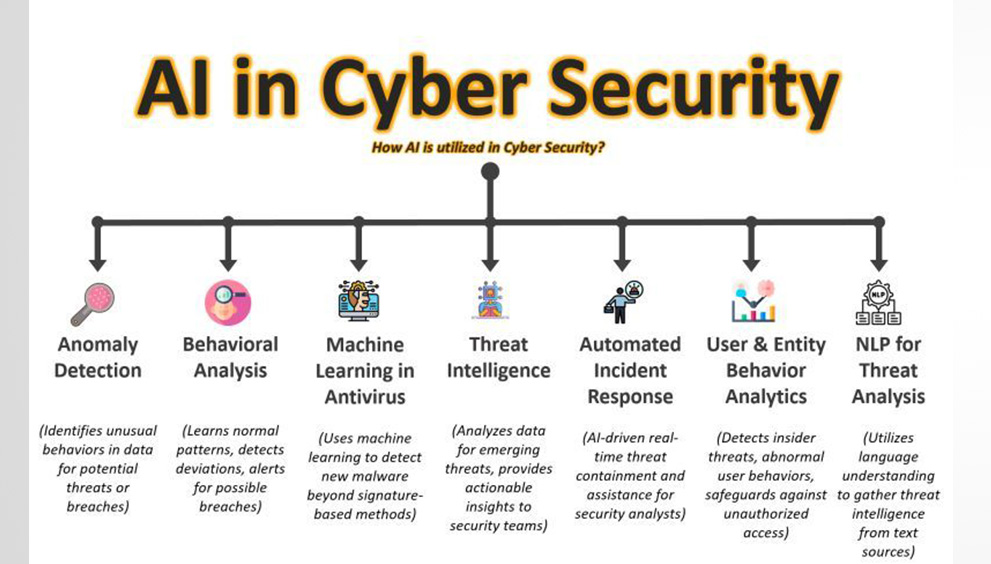
𝗔𝗿𝘁𝗶𝗳𝗶𝗰𝗶𝗮𝗹 𝗜𝗻𝘁𝗲𝗹𝗹𝗶𝗴𝗲𝗻𝗰𝗲 𝗶𝗻 𝗖𝘆𝗯𝗲𝗿 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗺𝗮𝗿𝗸𝗲𝘁 𝗶𝘀 𝗽𝗿𝗼𝗽𝗲𝗹𝗹𝗲𝗱 𝗯𝘆 𝗲𝘀𝗰𝗮𝗹𝗮𝘁𝗶𝗻𝗴 𝗰𝘆𝗯𝗲𝗿 𝘁𝗵𝗿𝗲𝗮𝘁𝘀, 𝗱𝗮𝘁𝗮 𝗰𝗼𝗺𝗽𝗹𝗲𝘅𝗶𝘁𝘆, 𝗮𝗻𝗱 𝘁𝗵𝗲 𝗲𝗳𝗳𝗶𝗰𝗶𝗲𝗻𝗰𝘆 𝗴𝗮𝗶𝗻𝘀 𝗯𝗿𝗼𝘂𝗴𝗵𝘁 𝗯𝘆 𝗮𝘂𝘁𝗼𝗺𝗮𝘁𝗲𝗱 𝗱𝗲𝗳𝗲𝗻𝘀𝗲 𝘀𝘁𝗿𝗮𝘁𝗲𝗴𝗶𝗲𝘀.
𝗔𝗜’𝘀 𝗖𝘆𝗯𝗲𝗿 𝗖𝗿𝘂𝘀𝗮𝗱𝗲: 𝗔𝗿𝘁𝗶𝗳𝗶𝗰𝗶𝗮𝗹 𝗜𝗻𝘁𝗲𝗹𝗹𝗶𝗴𝗲𝗻𝗰𝗲 𝗶𝗻 𝗖𝘆𝗯𝗲𝗿𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗠𝗮𝗿𝗸𝗲𝘁 𝗜𝗻𝘀𝗶𝗴𝗵𝘁𝘀 𝘂𝗽𝘁𝗼 𝟮𝟬𝟯𝟮 >>>
Artificial Intelligence in Cybersecurity refers to the integration of AI technologies like machine learning and pattern recognition into security systems. It enhances threat detection, risk assessment, and response mechanisms, bolstering digital defenses against evolving cyber threats.
𝗥𝗶𝘀𝗲 𝗶𝗻 𝗜𝗻𝘀𝘁𝗮𝗻𝗰𝗲𝘀 𝗼𝗳 𝗖𝘆𝗯𝗲𝗿 𝗧𝗵𝗿𝗲𝗮𝘁𝘀
Ongoing digitization is expected to increase with a fast pace in the coming years. One of the most significant and critical threats it poses is that our personal information is at risk like never before. As cyberattacks become more frequent and sophisticated, traditional security measures struggle to keep pace. AI in Cybersecurity employs machine learning to recognize evolving attack patterns, swiftly identifying anomalies and potential breaches. This proactive approach enhances overall defense mechanisms, ensuring timely mitigation of threats and minimizing potential damage.
𝗟𝗮𝗰𝗸 𝗼𝗳 𝗧𝗲𝗰𝗵𝗻𝗶𝗰𝗮𝗹 𝗘𝘅𝗽𝗲𝗿𝘁𝗶𝘀𝗲 𝗳𝗼𝗿 𝗔𝗜
Major industries are investing in AI but owing to dearth of in-house skilled talent, industries are lack to execute their AI strategies. The scarcity of AI-related skills hinders the growth of the Cyber Security market. Insufficient technical expertise limits effective implementation of AI-driven security solutions, obstructing optimal utilization and potentially undermining the sector’s potential to mitigate evolving cyber threats.
𝗗𝗮𝘁𝗮 𝗢𝘃𝗲𝗿𝗹𝗼𝗮𝗱
The digital landscape generates an overwhelming amount of data, making it challenging for human analysts to identify critical insights. AI processes and analyzes vast datasets at unprecedented speeds, detecting hidden correlations and anomalies that might indicate impending breaches. This enables cybersecurity teams to uncover threats that could otherwise remain undetected.
𝗔𝗿𝘁𝗶𝗳𝗶𝗰𝗶𝗮𝗹 𝗜𝗻𝘁𝗲𝗹𝗹𝗶𝗴𝗲𝗻𝗰𝗲 𝗶𝗻 𝗖𝘆𝗯𝗲𝗿 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗺𝗮𝗿𝗸𝗲𝘁 𝗶𝘀 𝗽𝗿𝗼𝗽𝗲𝗹𝗹𝗲𝗱 𝗯𝘆 𝗲𝘀𝗰𝗮𝗹𝗮𝘁𝗶𝗻𝗴 𝗰𝘆𝗯𝗲𝗿 𝘁𝗵𝗿𝗲𝗮𝘁𝘀, 𝗱𝗮𝘁𝗮 𝗰𝗼𝗺𝗽𝗹𝗲𝘅𝗶𝘁𝘆, 𝗮𝗻𝗱 𝘁𝗵𝗲 𝗲𝗳𝗳𝗶𝗰𝗶𝗲𝗻𝗰𝘆 𝗴𝗮𝗶𝗻𝘀 𝗯𝗿𝗼𝘂𝗴𝗵𝘁 𝗯𝘆 𝗮𝘂𝘁𝗼𝗺𝗮𝘁𝗲𝗱 𝗱𝗲𝗳𝗲𝗻𝘀𝗲 𝘀𝘁𝗿𝗮𝘁𝗲𝗴𝗶𝗲𝘀.
✅ 𝗗𝗼𝘄𝗻𝗹𝗼𝗮𝗱 𝗦𝗮𝗺𝗽𝗹𝗲 𝗥𝗲𝗽𝗼𝗿𝘁: https://lnkd.in/dy68-z8V
👉 𝗟𝗲𝗮𝗱𝗶𝗻𝗴 𝗖𝗼𝗺𝗽𝗮𝗻𝗶𝗲𝘀 𝗶𝗻 𝘁𝗵𝗲 𝗠𝗮𝗿𝗸𝗲𝘁:
▸ Palo Alto Networks
▸ Symantec
▸ IBM Security
▸ Cisco Systems
▸ McAfee
▸ Fortinet
▸ FireEye
▸ Trend Micro
▸ Darktrace
▸ CrowdStrike
▸ Cylance Inc.
▸ Samsung Electronics
▸ Intel Corporation
▸ Vectra AI, Inc.
▸ Xilinx Inc.
▸ Amazon Web Services
▸ NVIDIA Corporation
▸ Micron Technology
hashtag#cybersecurity hashtag#informationsecurity hashtag#smartsecurity hashtag#aiincybersecurity
hashtag#informationtechnology hashtag#marketresearch

 Member Login
Member Login