Navigating the New Frontier: Cybersecurity in the Age of Generative AI

Introduction
In today’s fast-paced digital era, generative AI has become a cornerstone of technological advancement, deeply entwined with the fabric of organizational functions. From creating personalized customer experiences to automating complex data analysis, AI’s applications span a vast array of industries, streamlining operations and opening new avenues for innovation. Its integration into business processes is not just a trend but a transformational shift, reshaping the way organizations operate and compete in the global market.
However, as with any technological revolution, generative AI brings with it a host of new challenges, particularly in the realm of cybersecurity. The very tools that empower companies to reach new heights of efficiency and creativity also pose unique threats. Cybersecurity, traditionally a game of cat and mouse between defenders and attackers, is now being reshaped by AI’s capabilities. As AI becomes more sophisticated, so do the potential cybersecurity threats, making it imperative for Chief Information Security Officers (CISOs) and their teams to understand and prepare for these emerging challenges.
In the subsequent sections, we delve into the specifics of these AI-driven cybersecurity threats and explore effective strategies and practical methods for CISOs to mitigate risks, ensuring the safety and integrity of their organizations’ digital assets.
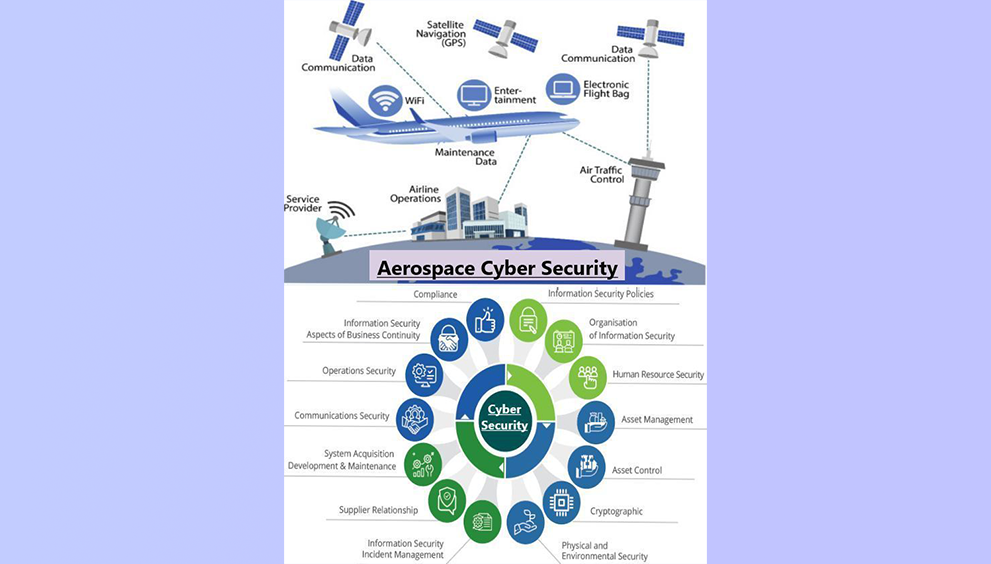
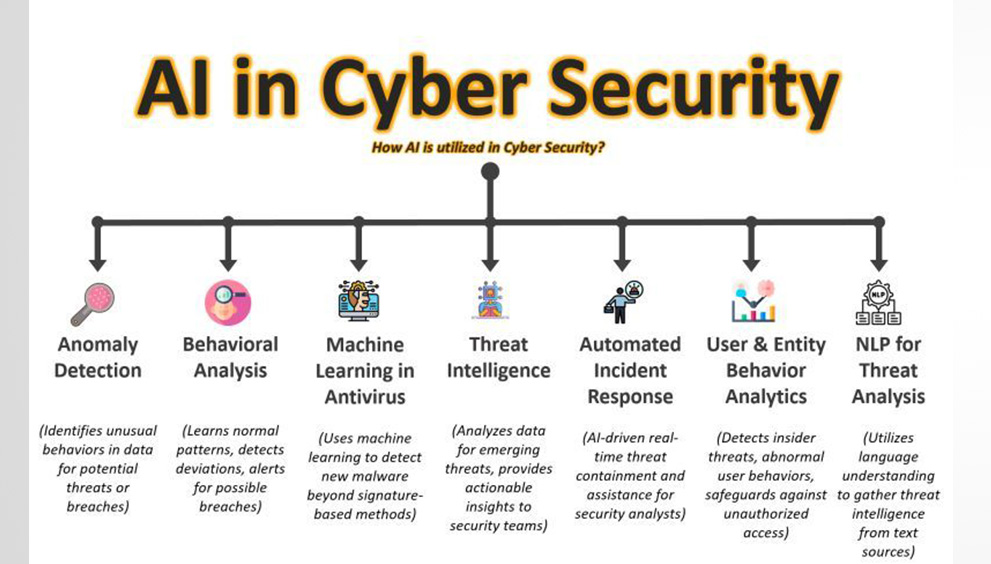
The Emerging Threats of Generative AI in Cybersecurity: Generative AI, while a boon in many aspects, has opened new frontiers for cyber threats. These advanced technologies have given rise to sophisticated methods of cyber-attacks, challenging traditional security paradigms.
- Deepfakes and Information Manipulation: One of the most unsettling developments is the rise of deepfakes. These AI-generated falsifications of audio, video, or text content are becoming increasingly indistinguishable from reality. For organizations, this poses a significant risk in terms of misinformation and reputation damage. Imagine a scenario where a deepfake video of a CEO making fraudulent claims goes viral, causing irrevocable harm to the company’s credibility.
- Automated Phishing and Social Engineering Attacks: Generative AI has also enhanced the capabilities of cybercriminals in executing phishing and social engineering attacks. By analysing vast amounts of data, AI algorithms can craft highly personalized and convincing phishing emails or messages, tricking even the most vigilant employees into divulging sensitive information.
- AI-driven Malware Development: Perhaps the most alarming is the potential for AI to automate and refine malware creation. AI algorithms can work in sync with basic reconnaissance tools, analyse the services/ports/security systems to identify vulnerabilities and develop malware specifically designed to exploit them. This could lead to a new wave of cyber-attacks that are faster, more efficient, and harder to detect.
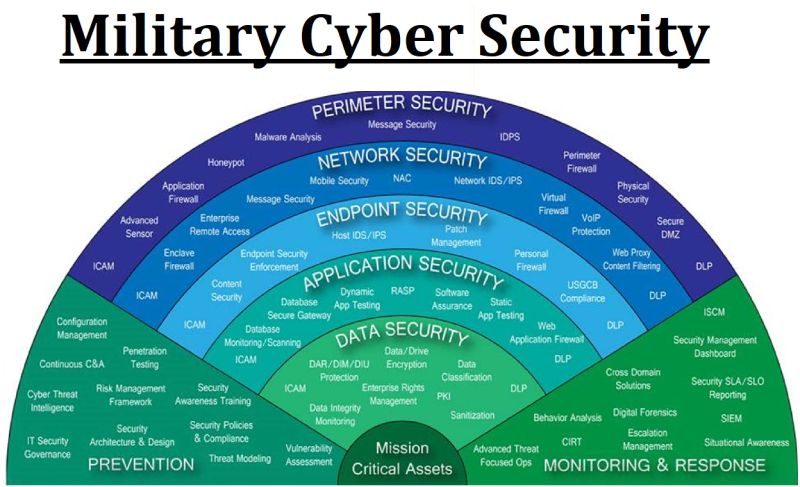
Strategies for CISOs to Mitigate Risks: As these AI-driven threats evolve, they outpace traditional cybersecurity measures, necessitating a more dynamic and proactive approach from CISOs and their teams. Recognizing these threats is the first step in developing effective strategies to counter them. And, in the face of these evolving AI-driven cyber threats, CISOs must adopt a multifaceted approach to bolster their organization’s cybersecurity posture. Here are key strategies to consider:
- Implementing Advanced Detection Tools: To counter the sophistication of AI-enabled threats, organizations must leverage Generative AI in their defence mechanisms. The recent developments from both Google and Microsoft in their Duet AI and Security co-pilot initiatives respectively, are the efforts in these directions. Similarly, all other security OEMs are building a flavour of generative AI in detection for the SOC teams. The advanced detection tools will utilize machine learning algorithms to identify and neutralize threats before they materialize. These tools can analyse patterns, predict potential attacks, and automate responses to security incidents, thus enhancing the overall security infrastructure.
- Regular Security Audits and Updates: Continuous assessment and updating of security protocols are crucial. Regular audits help in identifying vulnerabilities and gaps in the existing security architecture. Updating security measures, including software patches and system upgrades, ensures that defences stay robust against new threats. This proactive stance in maintaining and enhancing security frameworks is essential in keeping pace with the rapidly changing cyber threat landscape.
- Employee Education and Awareness Programs: Human error remains a significant vulnerability in cybersecurity. CISOs should prioritize comprehensive education and training programs for all employees. These programs should not only cover the basics of digital hygiene but also include training on recognizing and responding to sophisticated AI-driven attacks, such as identifying subtle signs of phishing attempts. Regular drills and awareness campaigns can significantly reduce the likelihood of successful social engineering attacks.
Practical Methods for Prevention: CISOs must employ both strategic and tangible methods to effectively mitigate AI-driven cyber risks. Incorporating advanced technologies and protocols is key to strengthening defence mechanisms. Here are some refined practical measures:
- Enhanced Identity Protection & Authentication Protocols: Beyond traditional passwords, incorporating implementing multi-factor authentication (MFA), biometric verification, machine validation and behavioural analytics for user validation is crucial. These measures ensure that access to sensitive systems and data requires more than just knowledge-based credentials, which AI can potentially mimic or generate. These methods greatly reduce the risk of unauthorized access, providing a robust barrier against credential compromise.
- Network Segmentation and Access Control: Segmenting the network into controlled zones limits potential breach impacts. Access should be tightly regulated, with stringent monitoring to ensure only authorized personnel access sensitive areas. This approach not only minimizes the attack surface but also confines any breaches, preventing widespread network infiltration.
- Data Loss Prevention (DLP) Tools: Implementing DLP tools provides granular control over data access and transfer. These tools monitor and protect data in use, in motion, and at rest, ensuring sensitive information is not lost, misused, or accessed by unauthorized users. By setting policies and controls, CISOs can prevent data breaches and leaks, significantly enhancing data security.
- Advanced Gateway Proxies: Utilizing advanced gateway proxies can provide additional layers of security. These tools offer deep visibility and control over web traffic and cloud applications, enabling organizations to detect and block malicious activities in real-time. They play a critical role in safeguarding against external threats and ensuring secure cloud usage.
- Regular Backups and Disaster Recovery Plans: Consistent data backups and a comprehensive disaster recovery plan are indispensable. They ensure minimal disruption and quick restoration of operations in the event of an attack, such as ransomware.
Presenting the Facts to the Board: As a CISO, effectively communicating the complexities of cybersecurity to the board is crucial, especially in the context of generative AI’s emerging risks. The focus should be on semi-technical aspects that directly correlate to business risks and outcomes. Here’s a guide to framing this discussion:
- Identifying Key Discussion Points: Start by outlining the specific threats posed by generative AI, such as deepfake risks, enhanced phishing attacks, and AI-driven malware. Explain these concepts in a business context, focusing on potential impacts like financial loss, reputational damage, and operational disruption.
- Business-Centric Risk Assessment: Provide a clear analysis of how these threats can affect the organization’s bottom line. Discuss potential scenarios and their implications on business continuity, data integrity, and compliance requirements. For example, the use of Generative AI tools can improve the productivity by 20% and can therefore directly impact the revenue positively. Similarly, non-availability of a set of resources for x number of days or loss of confidential customer data can impact the revenue negatively, directly or even through regulatory fines.
- Investment in Advanced Security Measures: Advocate for investments in new security technologies and protocols, such as DLP tools, advanced authentication methods, gateway proxies, identity management and network segmentation. Emphasize how these measures can safeguard against AI-generated threats, offering a return on investment through enhanced protection and risk mitigation.
- ROI and Cost-Benefit Analysis: Present a cost-benefit analysis of proposed cybersecurity enhancements. Highlight how proactive investment in security can be more cost-effective compared to the financial and reputational costs of a major breach.
- Aligning Cybersecurity with Business Strategy: Stress the importance of integrating cybersecurity into the overall business strategy. Cybersecurity should not be an afterthought but a pivotal aspect of the organization’s operational planning and risk management framework.
By adopting these strategies, CISOs can build a resilient cybersecurity framework capable of withstanding the challenges posed by generative AI. It is a continuous process of adaptation and learning, as the nature of cyber threats evolves in tandem with technological advancements. So a multifaceted approach, from understanding the use technology for both growth and exploitation, and the use of same technology for protection, while retaining the support of the stakeholders, is essential for CISOs to meet their organizational obligations.

 Member Login
Member Login