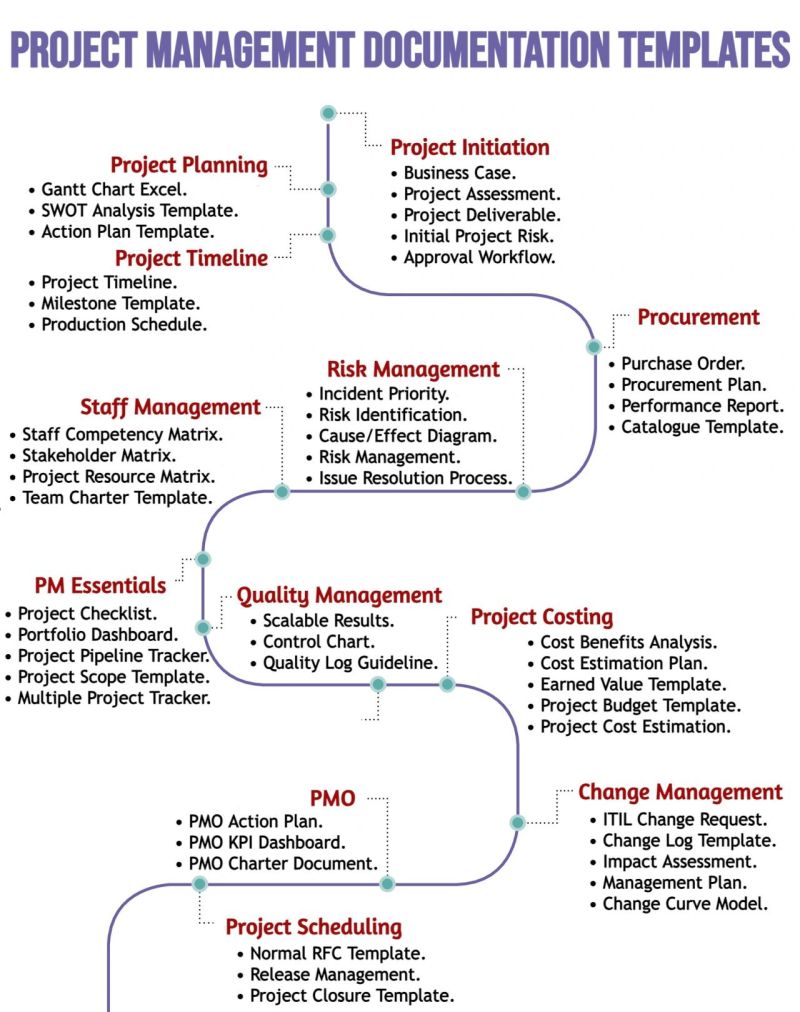
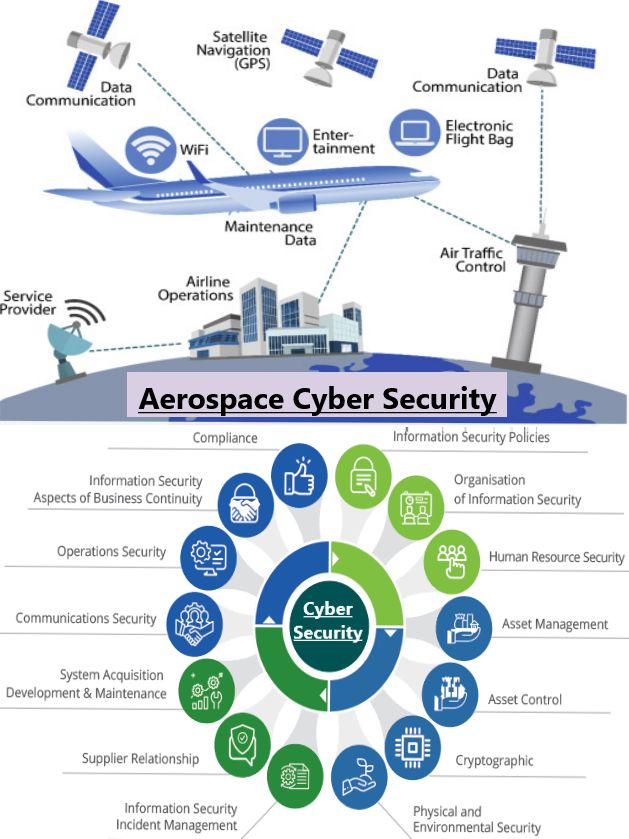
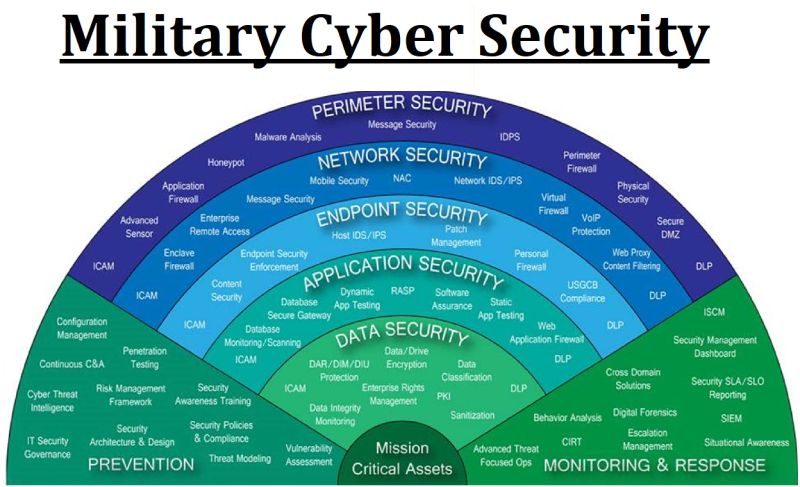
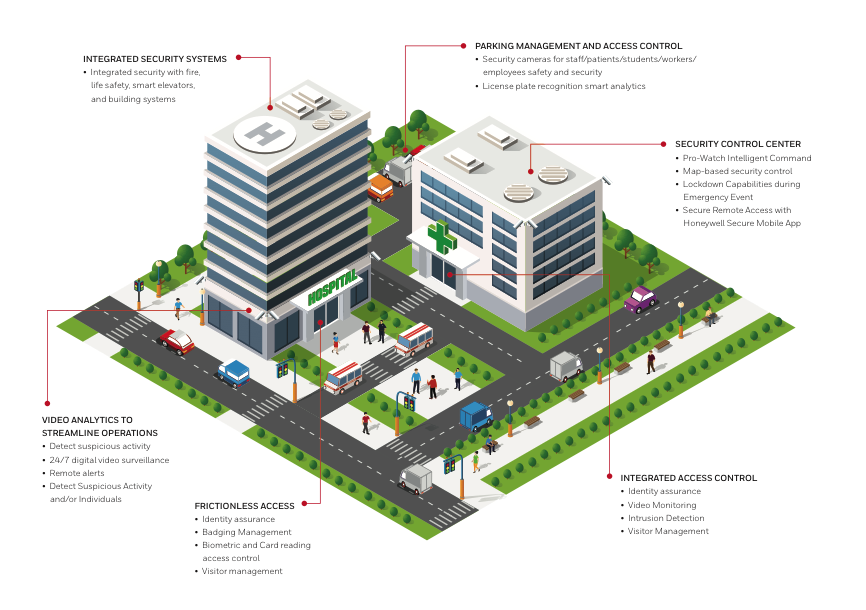
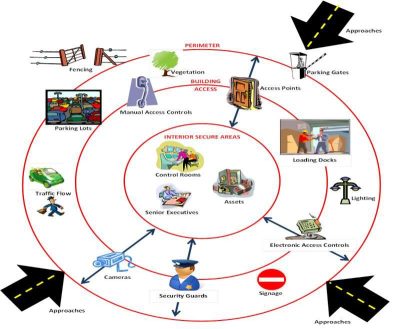
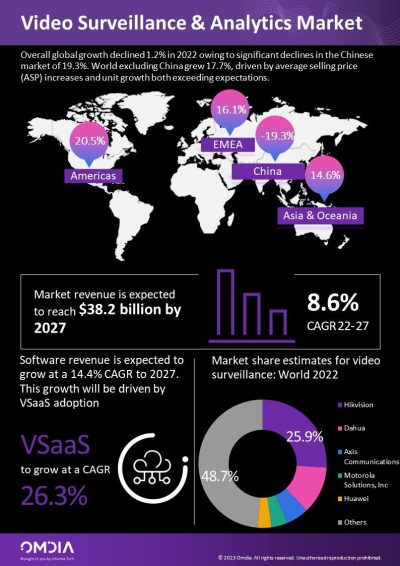
Understanding the Role of a Security Operations Center (SOC) in Cybersecurity 🔒
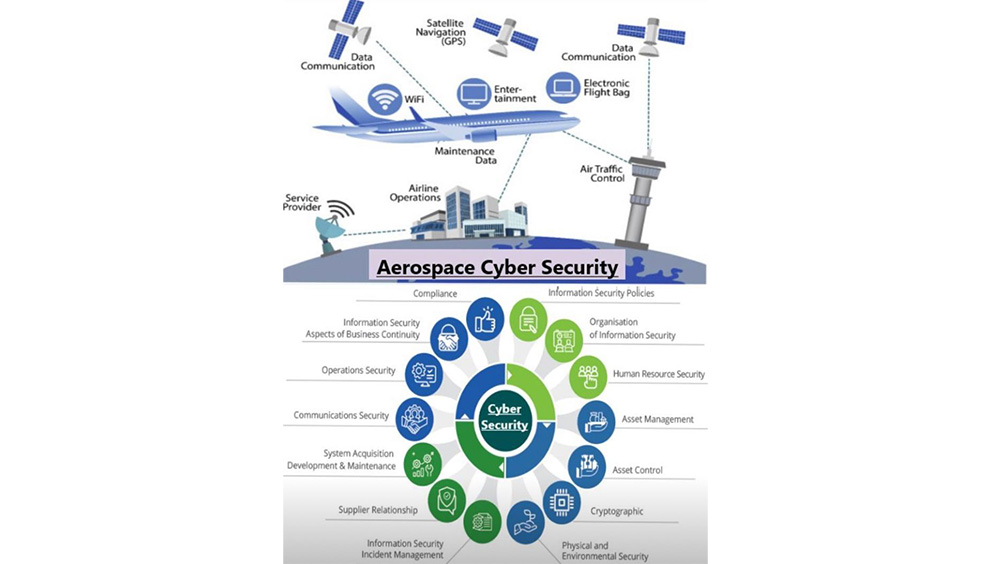
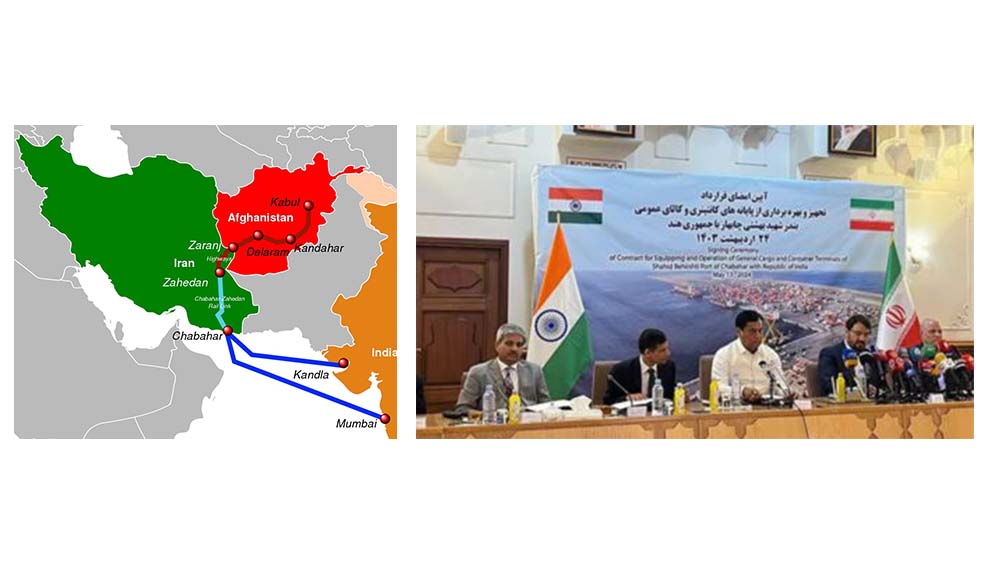
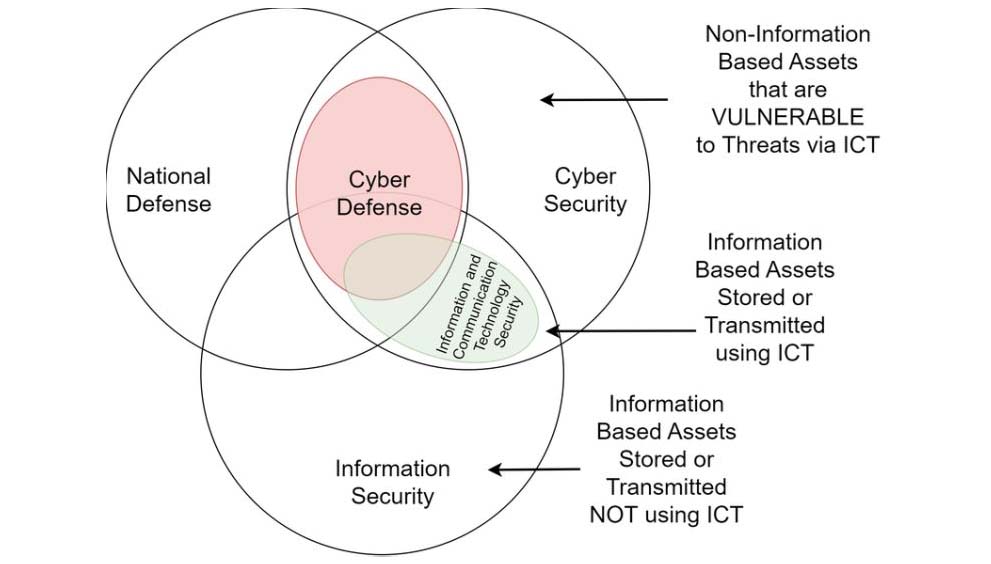
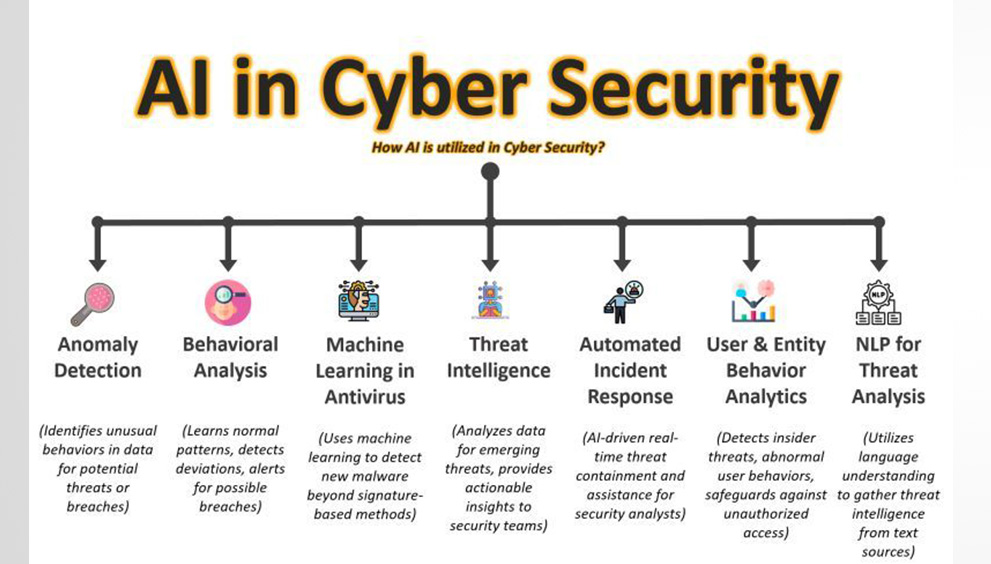
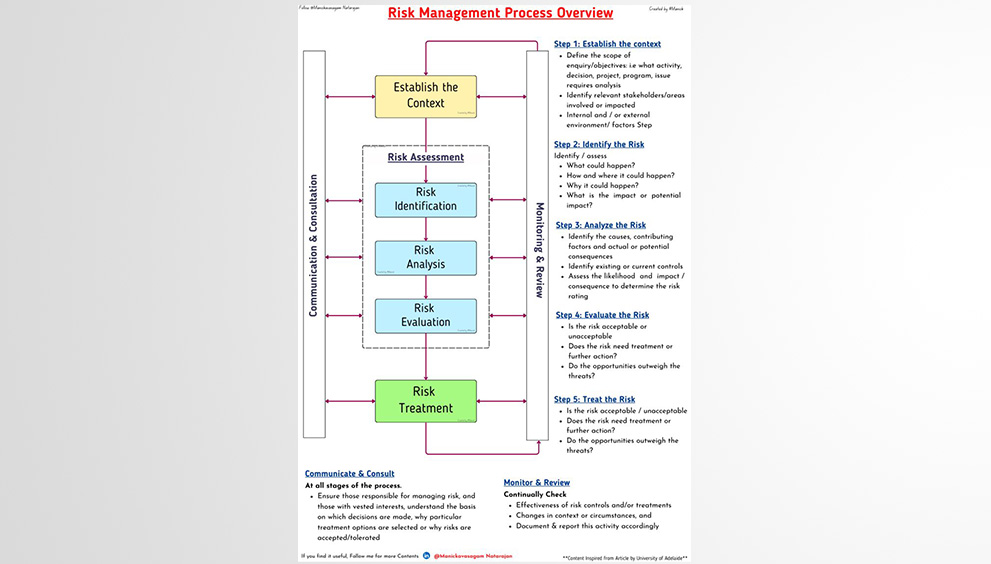
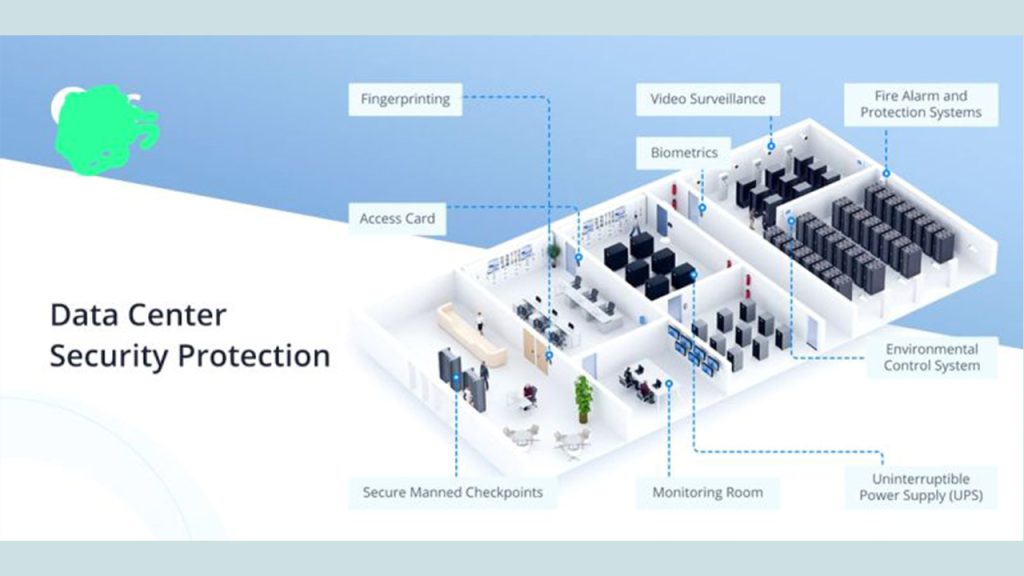
A Security Operations Center (SOC) is a team of IT security professionals that monitors a company’s network and systems 24/7. Here’s a snapshot of their key responsibilities and data sources: 📊 Key Responsibilities:1. Find Network Vulnerabilities 🛠️– Identify weaknesses in software or devices.– Example: Unpatched MS Windows computers. 2. Detect Unauthorized Activity 🚨– Monitor for […]

 Member Login
Member Login