Risk Advisory and Security Preparedness For Banking Sector In The Context Of Parliamentary Elections, India 2024.

By Commander Satyajit Roy. 07 April 2024.
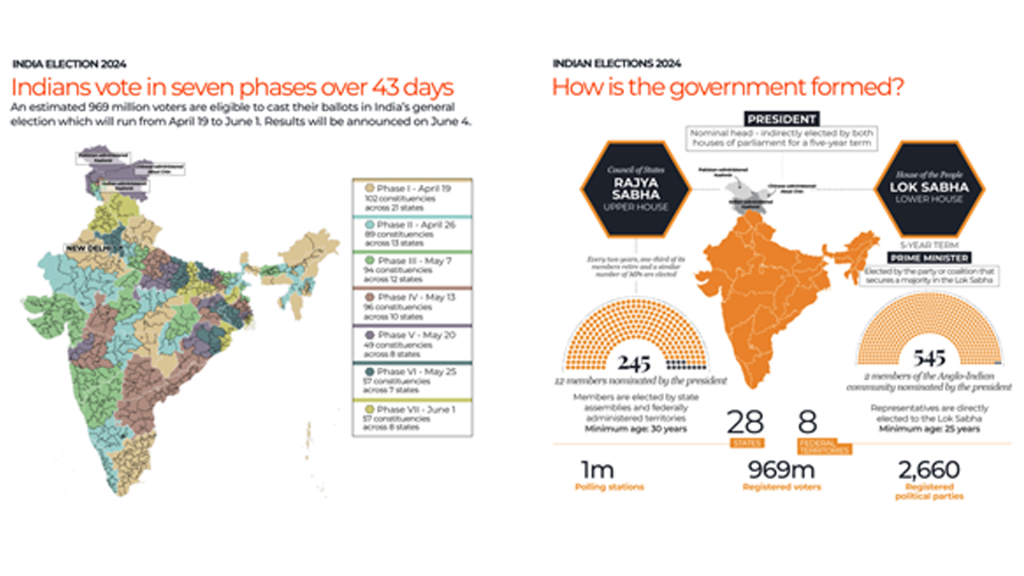
India to hold seven-phase general election from April 19, results on June 4, 2024. Prime Minister Narendra Modi is seeking a third straight term in the marathon six-week vote, the world’s largest democratic exercise.
In the run up to the parliamentary polls scheduled April until Jun 2024 and formation of a new Government at the Center thereafter, India i.e. Bharat, prepares for this mega even with all eyes and energy focused onto this singular mega event of the great ‘Dance Of Democracy’. Whilst acknowledging the heightened risk perceptions and security preparedness across all known and unknown counts, the whole country, braces up in their own manner to ride over this storm, smoothly and safely.
Security professionals look at this mega festival from their perspective of risks, threats, vulnerabilities and uncertainties and how they can meet the unseen and unexpected with confidence and fortitude.
In this article, Satyajit Roy shares his views on risk advisory and security preparedness for the banking sector in the context of upcoming parliamentary elections in India April to Jun 2024, with a focus on volatile states like West Bengal.
Risks, Threats And Vulnerabilities in Banking Sector
Given the context of upcoming Indian elections from April to June 2024, there are several security risk advisories that may be relevant across India, though scenarios is contextualized for West Bengal

Political Violence and Unrest: With elections come heightened political tensions, which can lead to incidents of violence and unrest. People should stay informed about local political developments and to avoid areas known for political friction.
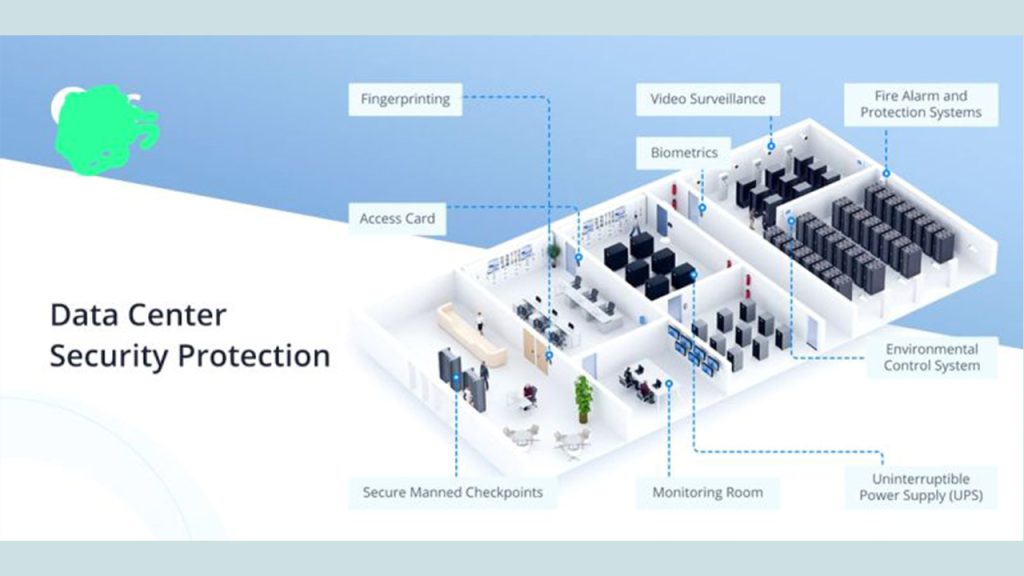
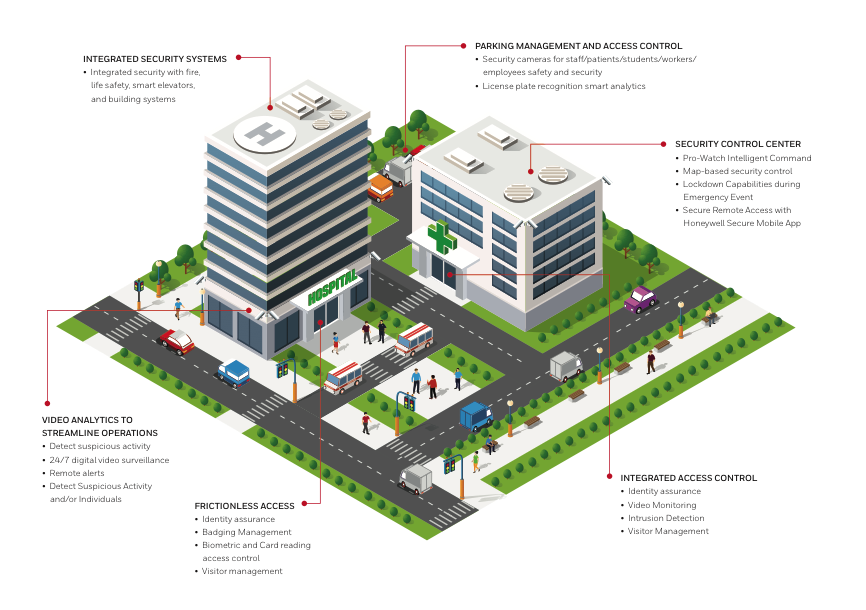
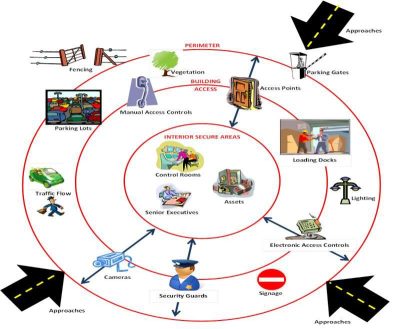
Physical Security Risks: Banks and ATMs may be susceptible to robbery, burglary or vandalism attempts, especially if they are located in areas with high crime rates or inadequate security measures. Insider threats, customer fraud and reputation assignation can damage the reputation and trustworthiness of banks and logistics services, leading to loss of customers and revenue.
Terrorist Threats: Elections may be seen as an opportunity for terrorist groups to carry out physical or cyber attacks or disrupt the banking process in any malicious way. Remaining vigilant and reporting any suspicious activities to authorities would thwart such attempts.
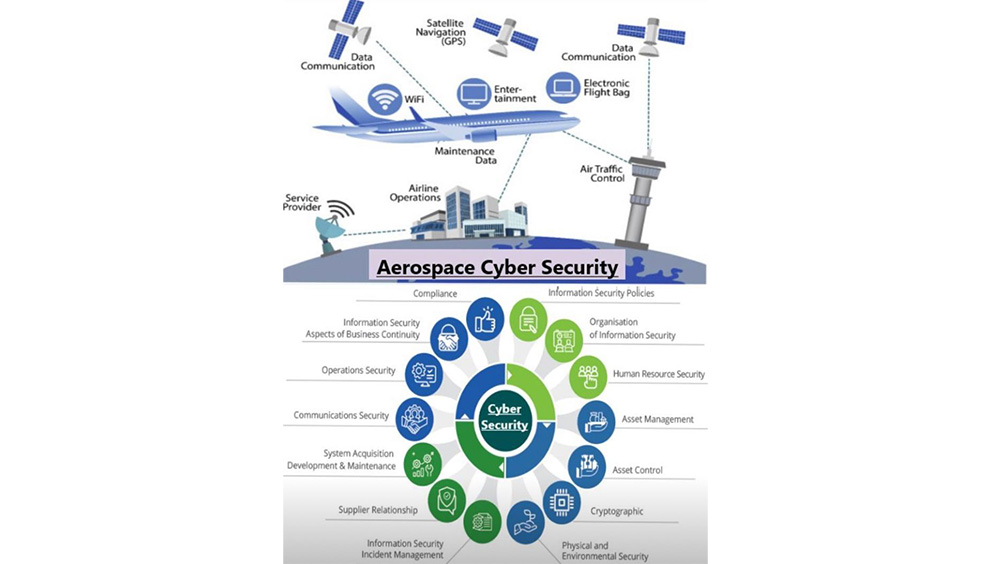
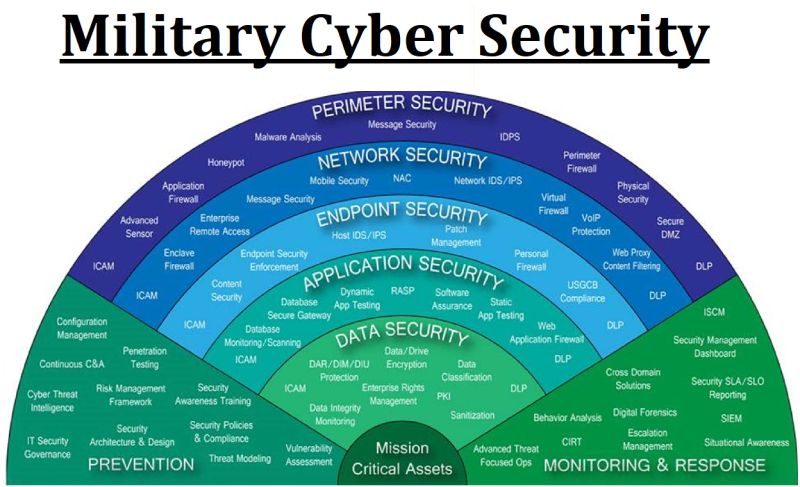
IT Security and Cyber Security Risks: There may be an uptick in cyber attacks targeting political parties, government agencies, or individuals involved in the electoral process. These activities may spill over to banking sector and cause unimaginable damage.
Social Media Disinformation: Elections are often accompanied by the spread of misinformation and fake news on social media platforms. Education and awareness about the risks of believing and sharing false information is necessary.
Social Security Risks and Communal Tensions: In diverse regions like West Bengal, communal tensions may flare up during election campaigns. Banking eco-system should be prepared to swiftly address any disruptions caused as an aftermath to incidents of communal violence and ensure unhindered banking services.
Travel advisories should be issued for specific areas where there is a heightened risk of election-related violence or instability. Key employees should avoid non-essential travel to these areas and to exercise caution if they must travel.
To mitigate these risks, banks, ATMs, and banking logistics services should implement comprehensive security measures, including physical security controls, robust cyber-security defenses, regular security audits and assessments, employee training and awareness programs, and incident response plans. Additionally, collaboration with law enforcement agencies and industry partners can help identify emerging threats and implement effective countermeasures.
Preparatory and Preemptive Measures
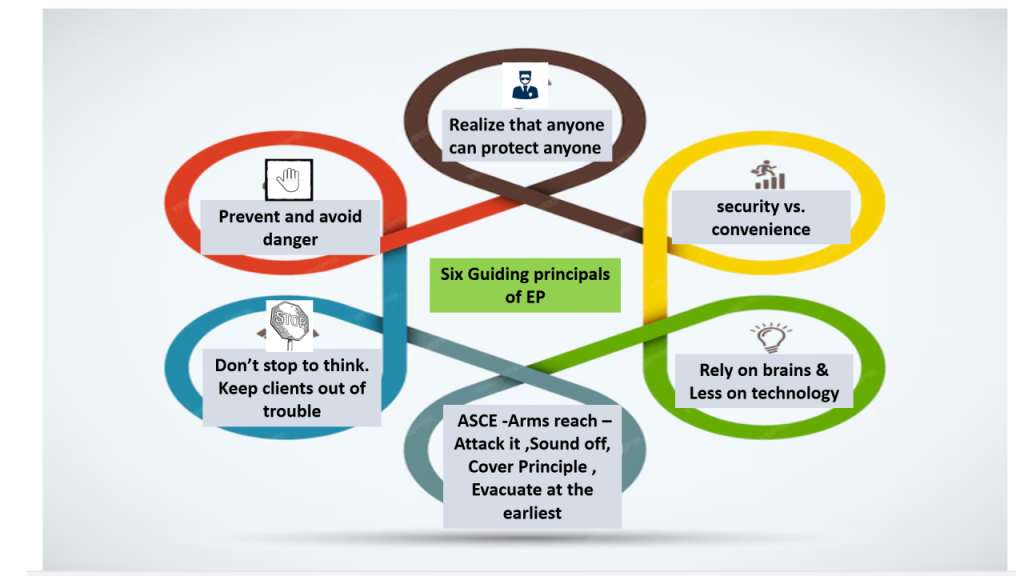
To prepare bankers and bank staff to effectively mitigate risks and respond to threats, comprehensive training and preparations are essential, in the user – operator – maintainer perspective.
General (Physical) Security Awareness Campaign
- Provide training on recognizing and responding to physical security risks, such as robbery, burglary, and vandalism.
- Educate employees about the importance of following security protocols, including proper cash handling procedures, alarm activation, and emergency response protocols.
- Conduct role-playing exercises and simulations to help employees practice their response to security incidents and reinforce key concepts.
Incident Response and Risk Mitigation
- Develop and rehearse incident response plans to ensure that employees know their roles and responsibilities in the event of a security incident or breach.
- Conduct tabletop exercises and simulated drills to test the effectiveness of incident response procedures and identify areas for improvement.
- Provide training on proper documentation, evidence preservation, and communication protocols during and after a security incident to support investigations and regulatory compliance requirements.
IT Security Safeguards
- Refreshing SOPs on best practices for securing network infrastructure, systems, and applications, including configuration management, patch management, and vulnerability management.
- Provide specialized workshops for IT professionals responsible for incident response, forensics analysis, and threat intelligence gathering.
- Implement comprehensive data backup and disaster recovery plans to minimize the impact of system downtime or data loss due to cyber attacks, hardware failures, or natural disasters.
- Enforce strict access controls to limit the exposure of sensitive data and prevent unauthorized access to critical systems
Cyber Security Awareness
- Offer training on identifying and avoiding common cyber threats, including phishing emails, malware, and social engineering tactics.
- Teach employees and users about the importance of strong passwords, secure internet browsing habits, and the risks associated with unauthorized software downloads or installations.
- Provide guidance on how to recognize and report suspicious activities or security breaches, such as unusual network behavior or unauthorized access attempts.
- Implement multi-factor authentication for employee access to critical systems and applications and prevent unauthorized access to systems.
- Conduct regular security assessments and penetration testing to identify and address weaknesses in IT systems and infrastructure.
Social Engineering Security Measures
- Comprehensive security awareness and training for employees to educate them about common social engineering tactics, such as phishing emails, phone scams, verification of customer identities, etc.
- Foster a culture of security within the organization by promoting accountability, transparency, and adherence to security policies and best practices at all levels.
Educate employees about common social engineering tactics used by fraudsters to manipulate individuals into divulging sensitive information or performing unauthorized actions.
Summary of Need and Action
Banks can adopt various risk mitigations and preventive measures to address the physical, cyber, IT, and social security risks they may be faced during periods of heightened socio-political activity. By implementing these risk mitigations and preventive measures, banks can enhance their overall security posture and reduce the likelihood and impact of security incidents and breaches.
By investing in comprehensive training and preparations, bankers and bank staff can enhance their skills, confidence, and readiness to effectively address the diverse risks and threats facing the banking industry today.
Familiarizing on the latest technologies, systems, equipment and controls is essential for best utilization of the hard and soft infrastructure investments made by Banks.
Stakeholders, Participants and Beneficiaries
The various stakeholders in the security threats and risk preparedness programs within the banking sector play crucial roles in ensuring the effectiveness and success of such initiatives. These stakeholders include:
Bank Management and Leadership. Bank senior executives, including CEOs, CTOs, and CISOs responsible for setting the strategic direction and priorities for security risk management within the organization. They provide leadership and support for security initiatives, allocate resources, and oversee the implementation of security policies, procedures, and controls.
Employees and Staff. All employees and staff members of the bank are stakeholders in security risk preparedness programs. They are responsible for adhering to security policies, following best practices, and reporting any security incidents or concerns. Employees participate in security awareness training, receive guidance on security protocols, and play a vital role in maintaining the overall security posture of the bank.
Physical Security Personnel, including security guards and surveillance operators, are responsible for safeguarding bank facilities, assets, and personnel against physical threats such as theft, vandalism, and unauthorized access. They play a critical role in enforcing access control measures, conducting patrols, and responding to security incidents in real-time.
IT and Security Teams security analysts, and cyber Security experts are directly involved in managing and mitigating security risks within the bank. They implement technical controls, monitor network infrastructure, analyze security threats, and respond to incidents to protect against cyber attacks and data breaches.
Government Administration and Departments, law & Order Enforcement Organizations, Regulatory Authorities and Compliance Officers including banking regulators and government agencies, establish security standards, guidelines, and regulations that banks must comply with to protect customer data and maintain financial stability. Compliance officers within the bank are responsible for ensuring that security policies and procedures meet regulatory requirements and industry standards.
Customers and Account Holders entrust banks with their personal and financial information, making them stakeholders in security risk preparedness programs.They expect banks to implement robust security measures to protect their data, prevent fraud, and ensure the confidentiality and integrity of their accounts and transactions.
Service Providers, Vendors and Business Partners that work with the bank may have access to sensitive data or systems, making them stakeholders in security risk management efforts. Banks collaborate with vendors to assess their security controls, manage third-party risks, and ensure compliance with security standards and contractual obligations.
Industry Associations and Collaborative Forums and information-sharing platforms bring together banks, security professionals, and experts to exchange knowledge, best practices, and threat intelligence. Banks participate in these collaborative initiatives to stay informed about emerging threats, benchmark their security programs, and enhance their resilience through collective action.
By engaging and collaborating with these stakeholders, banks can create a culture of security, build trust with customers, and effectively manage security risks to safeguard their reputation, assets, and operations.
Objectives and Outcome Of Advisory Notice
- To Be Informed. Experts in the field share best practices, expert opinions, analysis, and industry trends
- To Stay In Control. Gain understanding of contemporary security best practices in Banking Sector.
- To Network. Meet with valuable stakeholders
Risk Advisory & Security Preparedness For Banking Sector In The Context Of Parliamentary Elections, India 2024.
by Commander Satyajit Roy. +91 9830749436 | cdrsatyajitroy@gmail.com | Kolkata. 07 April 2024.

 Member Login
Member Login