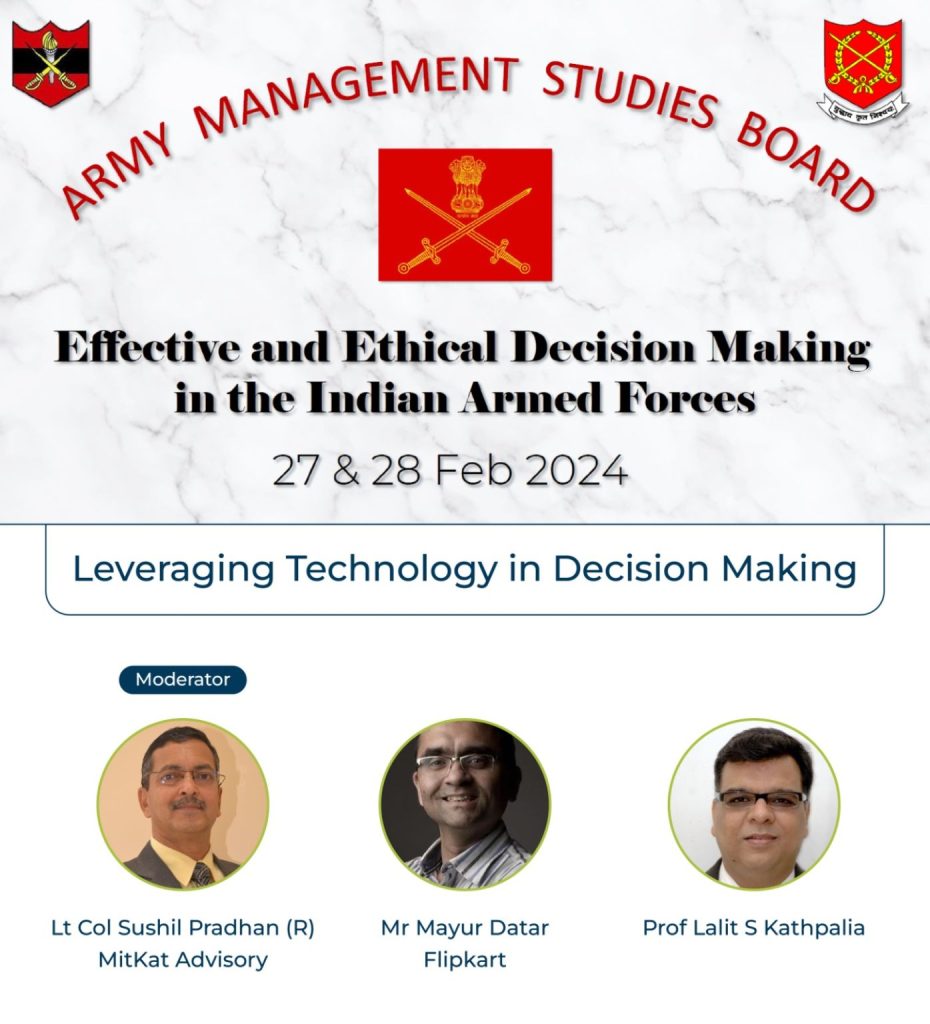
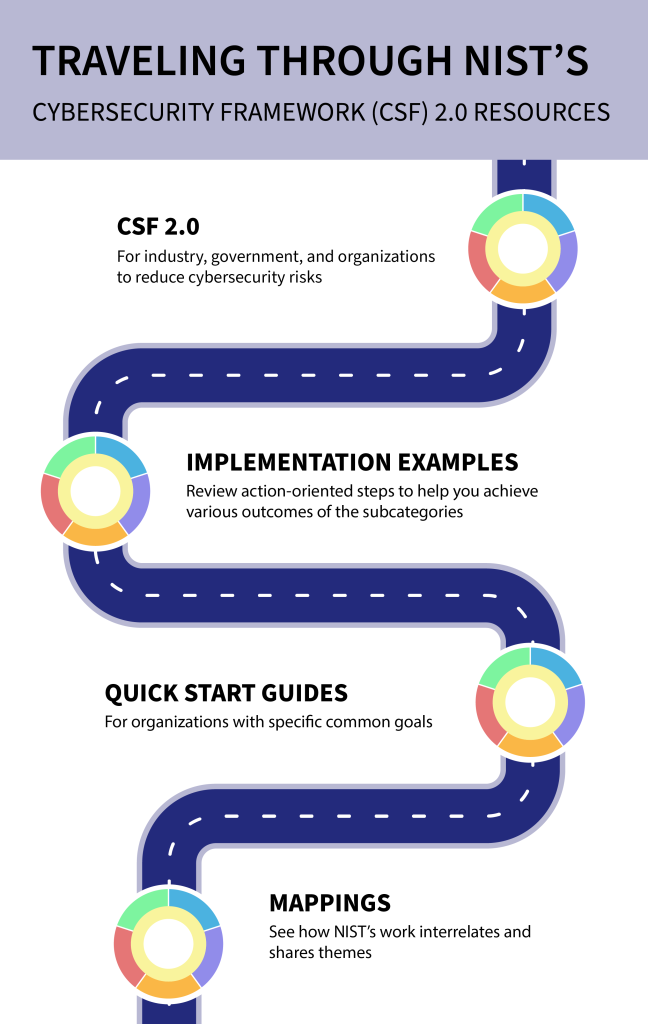
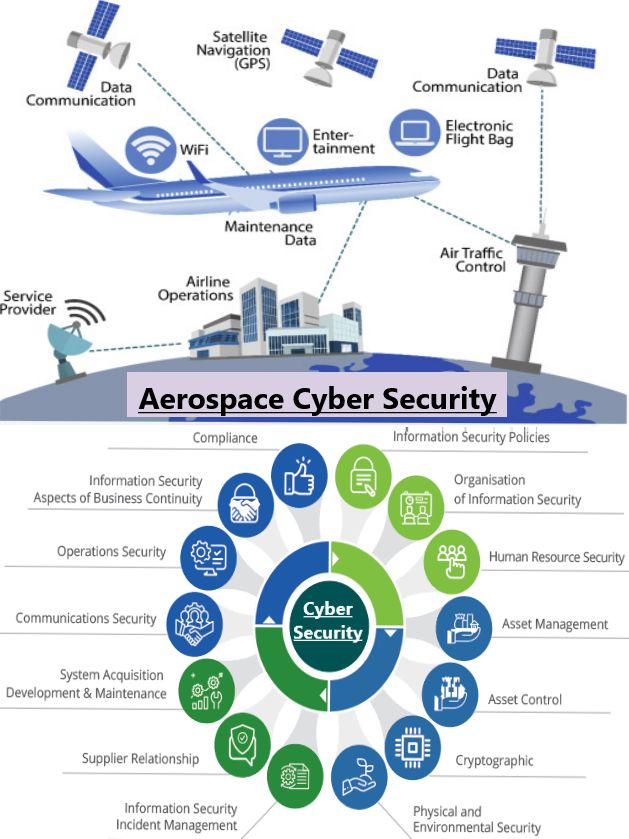
Cybercrime has become increasingly sophisticated in recent years, with scammers employing a variety of tactics to deceive and defraud unsuspecting individuals.

Col (Dr.) Inderjeet SinghCol (Dr.) Co-Founder India Blockchain Forum, Representative to UN Office at Geneva | India’s Top 30 Blockchain Think Tank
#CyberArrest: Deceptive Tactics of Impersonating As Law Enforcement in hashtag#OnlineScams
hashtag#Cybercrime has become increasingly sophisticated in recent years, with scammers employing a variety of tactics to deceive and defraud unsuspecting individuals.
🎒 🎒One such scheme that has gained traction in the digital realm is the “hashtag#DigitalArrest” or hashtag#CyberArrest scam.
This deceptive ploy involves fraudsters impersonating as law enforcement officials to manipulate victims into handing over money or personal information.
In this article, we delve into the intricate workings of the CyberArrest scam, explore how scammers exploit psychological tactics to prey on their victims, examine the methods they use to gather personal information, and discuss strategies for safeguarding oneself against such fraudulent activities.
📌The CyberArrest scam typically begins with a seemingly innocuous message or phone call, often via WhatsApp, from someone claiming to be a police officer. The fraudster may use a hashtag#fakeprofile picture depicting an individual dressed in a police uniform to lend credibility to their impersonation. This initial contact sets the stage for the manipulation to follow.
Read full Article – https://www.linkedin.com/pulse/cyber-arrest-deceptive-tactics-impersonating-law-online-singh-9yugc/?trackingId=6Fz%2BDrwFTrKNYjnRsm3Wew%3D%3D

 Member Login
Member Login