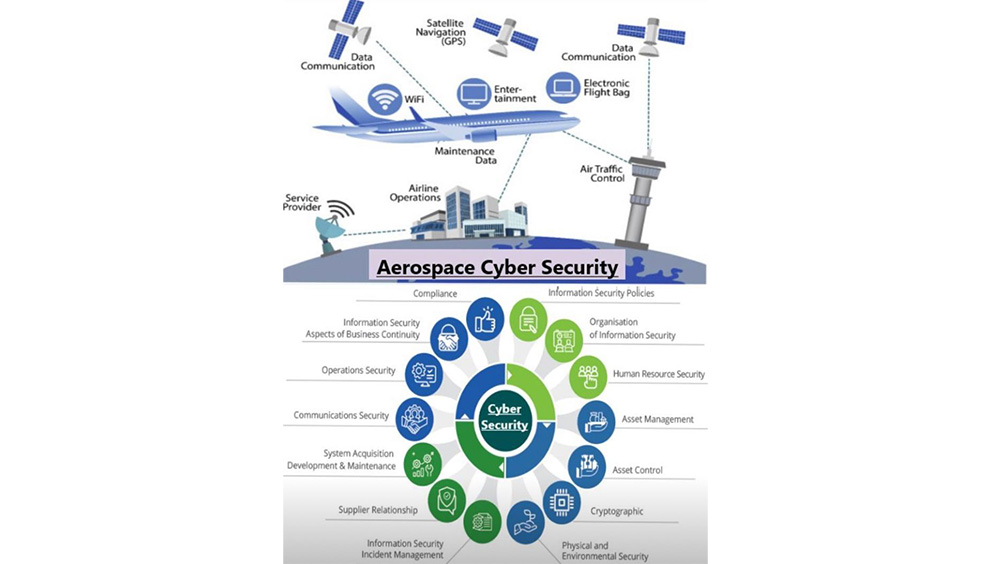
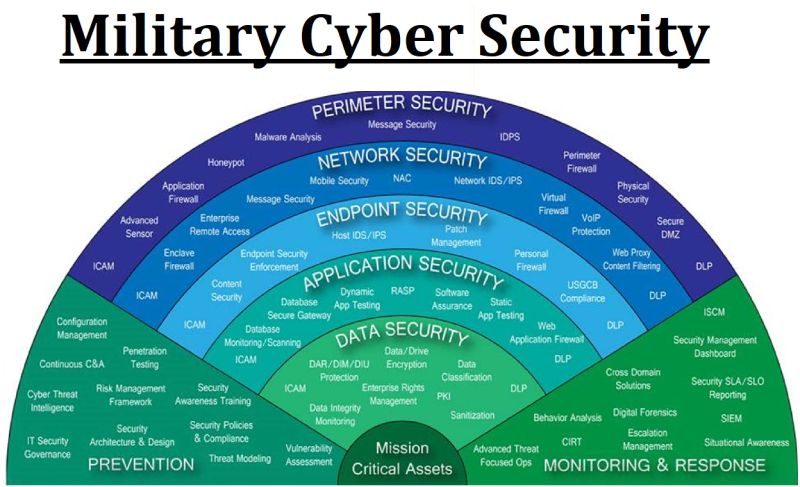
BASELINE SECURITY STANDARDS


Baseline security standards are the minimum standards to which a security programme should conform irrespective of the level of risk.The security risk analysis then determines the extent to which the baseline standards should be built upon.
Businesses implement different #baselinesecuritystandards and their benefit is contingent to the extent of which they are being used and the capability optimized.
A typical baseline security management standard should include and not limit these elements :-
➡️ Security focal point –A security personnel such as a security manager etc should be designated as a security focal point.Personnel assigned as a sfp should be well trained and meet relevant competency requirements.
➡️ Procedures – Security measures should be considered in all operational procedures.The security aspect of operational procedures should be determined by line management responsible for that operation and the sfp.
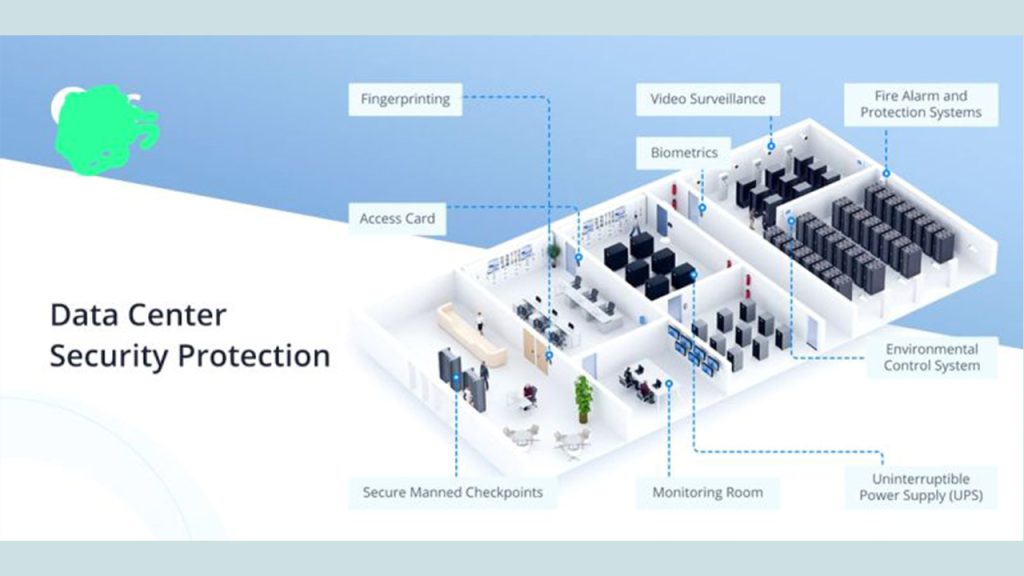
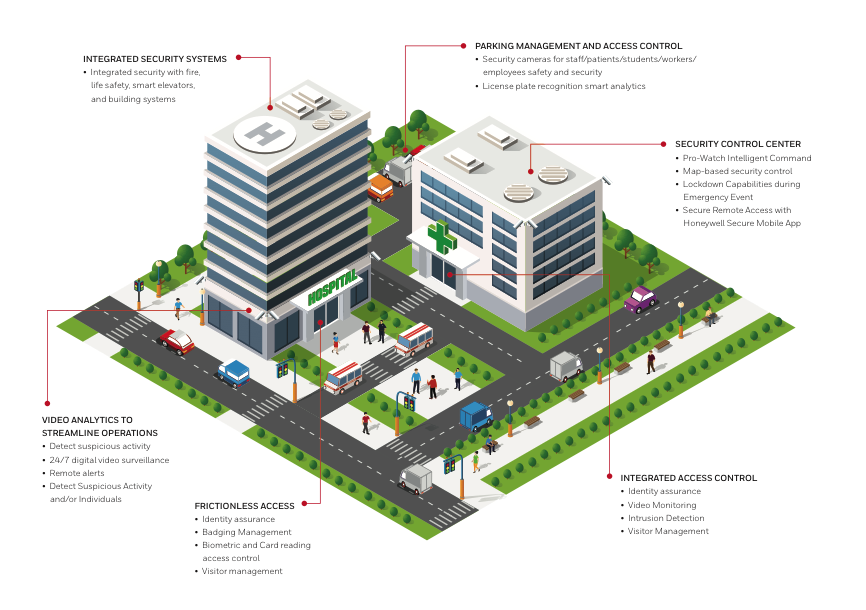
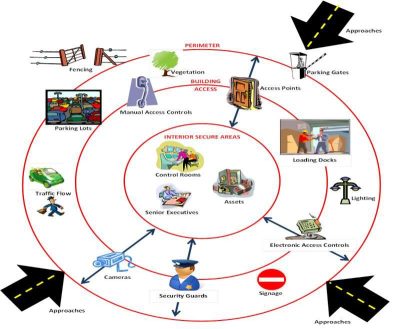
➡️ Access management –Access of premise should be through designated and controlled access points, and should be documented through the use of automated access control systems or a manual register.Additionally Aacs should restrict unauthorised access in critical points, as well as provide automated audit trail.
➡️ Key control –A procedure should be in place to control the issue of keys, which should only be issued to designated authorised persons, upon signature.A register should be kept documenting all key issues and returns, and this should be checked to monitor deviances.
➡️ Site perimeter –The site perimeter should clearly demarcate company property.The extent of perimeter protective measures should be in accordance with the nature of the site and local sfp expert recommendation.
➡️ CCTV surveillance -The use of CCTV surveillance should be at the discretion of the local management team, and in consideration of local laws and cultural norms. Where surveillance systems are installed, signs should be prominently displayed.
➡️ Alarm system – External doors and windows of critical areas should be fitted with alarm sensors.Signs and alarms sounding boxes should be prominently displayed.
➡️ Exterior lighting –Exterior lighting should be employed to ensure the safety of personnel and serve as deterrent to intrusion and to assist in the detection of intruders.
➡️ Guarding contractors –The guarding contract should be supplemented by a service level agreement.
➡️ Pre-employment screening – All potential hires should be screened
➡️ Information security –Information security procedures should be followed by all.Sensitive information should be locked away or encrypted.Sensitive waste should be securely disposed of by cross-shedding and a clear desk policy should be in place.
➡️ Integrated systems –They should meet today’s requirements and meet the business needs into the future.They should reduce cost and provide a return on investment by eliminating costly manual processes.
#securityskills #capsiBy Arshley Susan Wanjiku CSMP®, M.ISMI®. Security Risk Management Consultant and Thought Leader at Lakewood Solutions Co.

 Member Login
Member Login