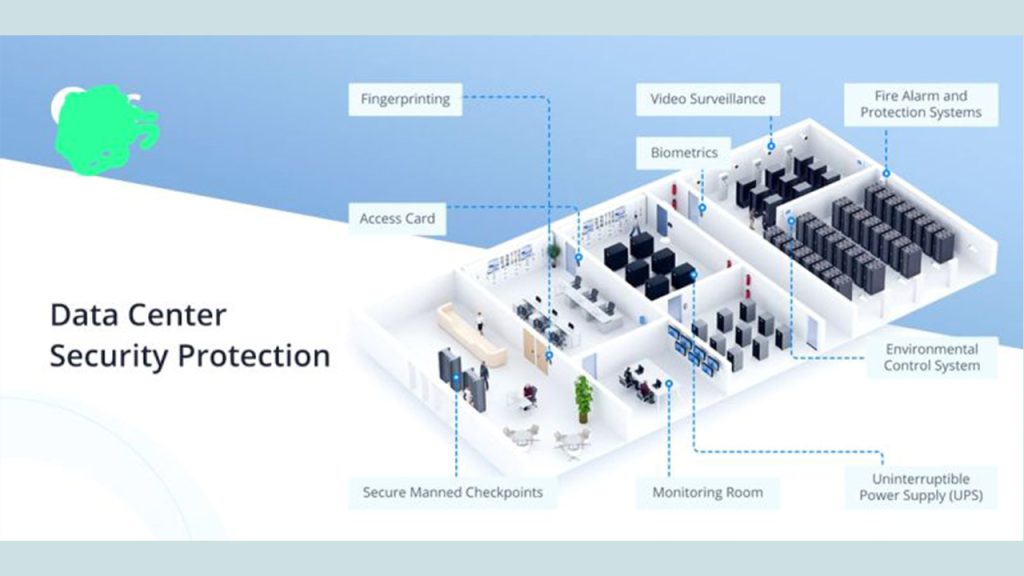
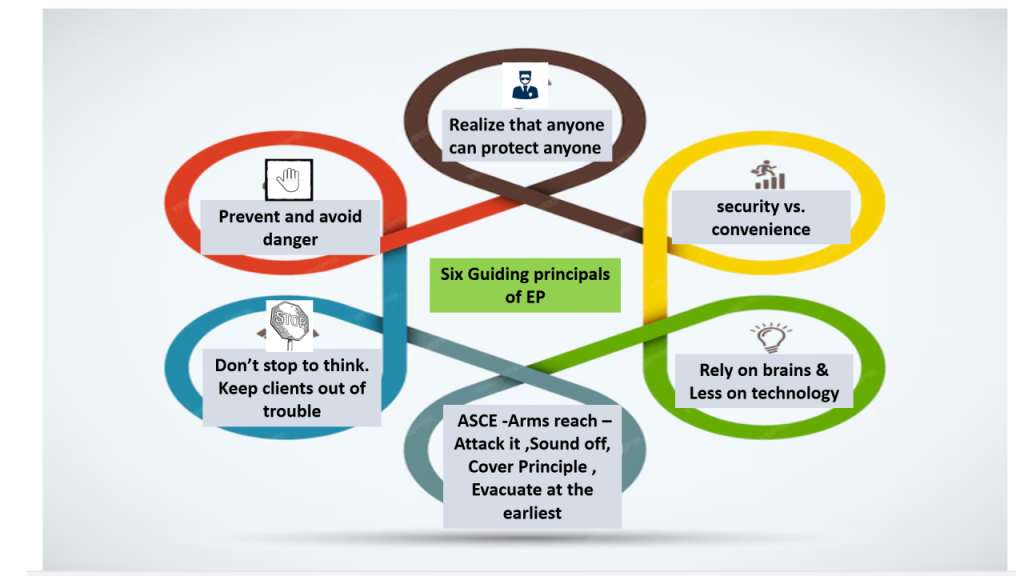
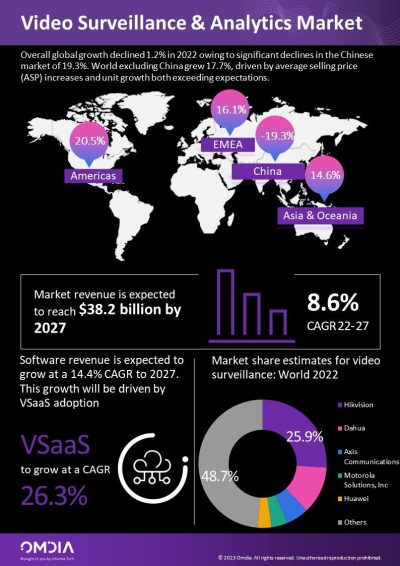
6 Tips for Building a Physical Security Operations Center Learn about six key tips on how to establish the right mindset before building a security operations center (SOC)—a critical first step for security leaders.

CORPORATE RISK, SECURITY OPERATIONS CENTER
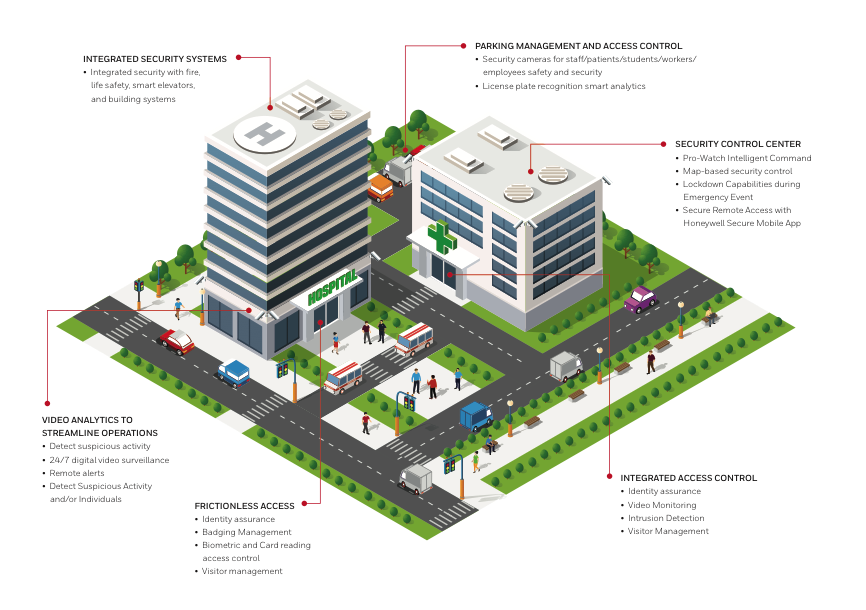
Since leaving the British Army five years ago to work in corporate security and risk management, I’ve heard numerous security leaders make a strong case for why they should or should not create a security operations center (SOC). While the benefits of a SOC are clear—including a stronger security posture and better visibility of potential risks—not every organization feels the need or is ready to centralize their security operations.
Those that are typically fall into one of two categories:
- Their organization has reached a critical mass of infrastructure, people and reputation that now requires more oversight and control.
- They had previously relied on a well-connected network of regional and country security managers to identify and manage risk at a local level, but are now in need of a more centralized approach.
Recent events and challenges—from new and increased risks spurred by the COVID-19 pandemic to a rise in the number and sophistication of cyber attacks—have also made a strong case for building a SOC.
Regardless of the reasons why, experience has taught me that building a SOC requires security and risk leaders to first establish the right mindset. Below you’ll find six key tips for how to do so. Keep in mind that this is not meant to be an exhaustive how-to list, but rather a quick look at what you, as security and risk professionals, need to know and do to successfully centralize your security operations.
No. 1: Assume nothing
You likely have an existing security network that you can build your SOC around or upon. However, the SOC will be a new operational model with new ways of working, so don’t assume everyone in the organization will understand what a SOC is or what it is meant to do.
Instead, assume no one knows anything about what the SOC is and how you will build it. At the outset, be sure to obtain buy-in from all stakeholders, carefully manage your messaging and establish clear lines of communication between the SOC team and key business lines and partners.
No. 2: Reinforce the importance of speed and accuracy
High-performing SOCs are fueled by accurate, real-time information. It’s difficult to fully test accuracy and speed of information prior to activation, and leaders should be prepared to have shortcomings exposed in real time. While this is one of the biggest challenges of getting your SOC up and running, it is also one of the easiest to solve.
Resist the urge to operate under the premise that every piece of information that comes into the SOC will only be known to the SOC. It’s a common error that leads to information hoarding, for fear of disrupting people. This can be avoided by establishing a culture whereby disrupting or distracting business partners a few times is infinitely better than shocking or surprising them one time.
As a best practice, determine:
- What needs to be done immediately with the information
- What the second and third order effects are
- Who else in the business other than the immediate security ecosystem needs to know the information
No. 3: Provide capability for the people—don’t attach people to capability
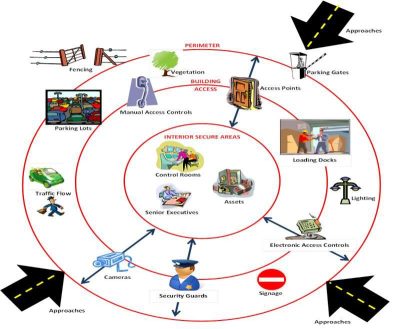
There is a seemingly endless array of enabling technologies to support security operations. When combined with internal monitoring systems, the technology can feel like it is driving you rather than the other way around. Take control by mapping out:
- What is needed to help create a degree of foresight
- What is needed to identify events as they happen
- How to enable the flow of the information and intelligence that is being created, by meshing technology with people
In an ideal world, there would be seamless integration and workflows with minimal information overlaps, but it rarely works out that way. Having a clear end state, operation model and systems architecture built around people will allow you to be clear-eyed about your decisions.
No. 4: Aim to add value
Security is a cost center. The first question your leadership team will likely ask is, “How much?” To steer the conversation in the right direction, create a business plan that shows the value of the SOC across the organization. It’s critical that you look beyond your team and identify opportunities that support other parts of the business.
Key questions to surface the SOC’s added value are:
- Where can I create relationships, both tangible and intangible, to contribute to the business case?
- How can I help other business areas deliver value more effectively without threatening their own expertise or capabilities?
- How can I imaginatively pull on an existing capability and build partnerships to support it?
At first glance, there is a good chance that it will seem as though most of the SOC’s costs will be covered by centralizing security operations, and efficiencies gained as a result. This assumption will cost more than you think—especially if you are adding 24/7 security coverage—making it more critical that you clearly articulate the value the SOC will deliver.
No. 5: Build in redundancy from the start
You will inevitably be asked to do more than you are capable of. This means that it’s necessary to carve out time for your team to process information and think critically about its impact. Teams that operate under extreme pressure or work continuously make mistakes and miss things.
Your SOC can’t afford either, especially in the early days. But new systems and workflows take time to learn, adjust and optimize. Build in enough operational redundancy to give your team the time it needs to fluctuate capacity with the inevitable ebb and flow. The team will then be able to pivot or accelerate the SOC’s operating tempo when a crisis comes along.
No. 6: Create a SOC fit for tomorrow
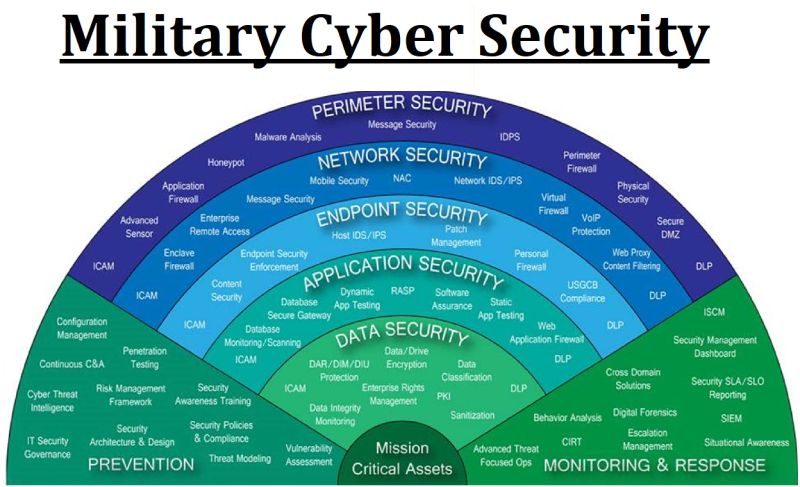
There are many ongoing debates and conversations about whether cyber and physical security SOCs should be combined. I’ve been part of several such conversations and know firsthand how complicated it can be to try and converge two separate SOCs. They are built around different principles, segmented by different functions, and can be in different physical locations with different operating procedures.
When building your SOC, consider how it might serve future needs. Technology that is fit for purpose today might not be fit for purpose tomorrow. Money saved by making investments in technology that is “good enough for now,” can quickly become insufficient, causing you to to rethink your security strategy.
Create a roadmap for your SOC and review the roadmaps of both your partners and suppliers. Then ask yourself:
- Is my organization likely to converge cyber and physical security in the near future?
- What can I do to move the convergence conversation forward?
- How can I be a catalyst for change rather than the recipient of it?
Most importantly, how can you future-proof your SOC against the next big risk or disruption?

 Member Login
Member Login